User Input
Description
User Type: Selecting one of the following user types is mandatory.
Regular
When you select the Regular user type, the user is granted full access to assets and all required permissions for Vulnerability Management, Detection and Response (VMDR), Policy Compliance (PC), CyberSecurity Asset Management (CSAM), Global AssetView (GAV), Cloud Agent (CA), and Unified Dashboard (UD) applications or modules.
Note: By default, the Regular Manager has managerial access to Vulnerability Management (VM) and Policy Compliance (PC).
In addition to VM and PC, you also have access to CSAM, GAV, CA, and UD from API. However, you can choose to select or deselect them from the UI.
Super
When you select the Super user type, the user is granted full access to assets and all required permissions for all modules or applications.
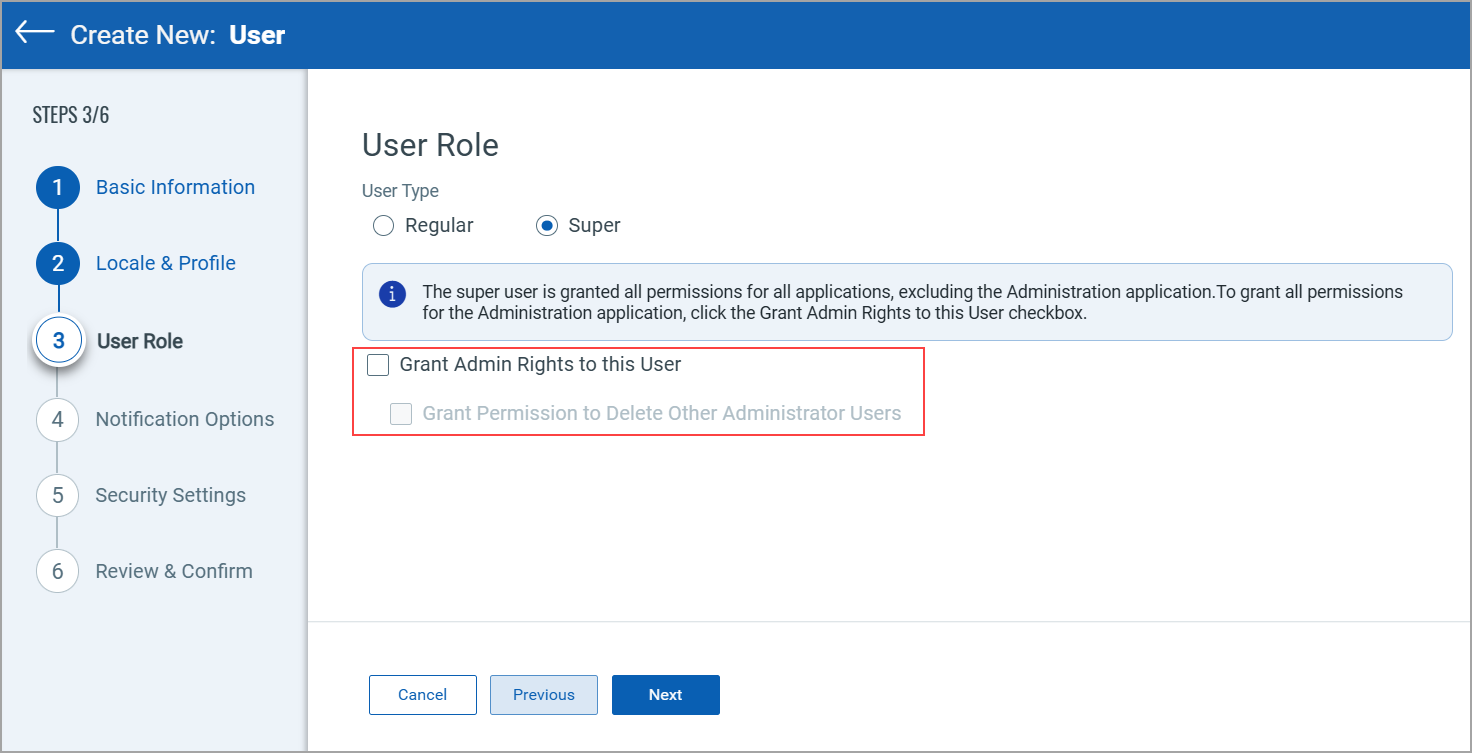
Note: The super user is granted all permissions for all applications, excluding the Administration application.
- Click the Grant Admin Rights to this User checkbox to grant permission to fully access the Administration module or application.
- Click the Grant Permission to Delete Other Administrator Users checkbox to grant permission to delete other administrator users.
User Role
Select the required user role from the User Role list.
The supported values are Manager, Unit Manager, Scanner, Reader, Remediation User, Contact, User Administrator, and Auditor.
Important:
- When you create a user with the User Administrator role, the user is granted the privilege to edit and provide the required permissions to any user within the subscription.
- Additionally, you can grant this user permission to delete other administrator users by clicking the Grant Permission to Delete Other Administrator Users checkbox.
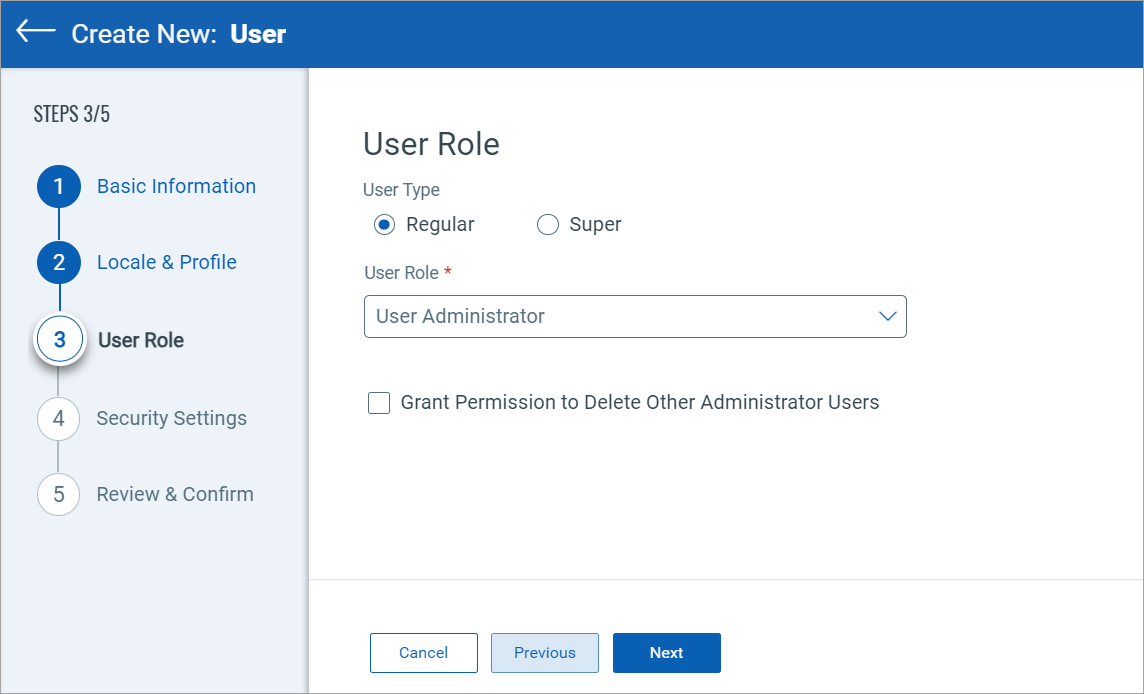
- None of the following user input elements mentioned in this table are shown for the user in the User Administrator role.
Additional Roles
Select the checkboxes next to the roles listed in the Unassigned Roles section and click the arrow to move them under the Assigned Roles Section.
By doing so, you can provide additional or custom roles apart from the default roles.
Allow Access To
Select the checkboxes next to GUI and API based on whether you want to grant the user the UI or APIFor access, or both.
Business Unit
Select the Business Unit from the Business Unit list.
Note: The Business Unit list is shown only for the User Roles - Unit Manager, Scanner, Reader, and Remediation User.
Allow user view access to all objects
Select the checkbox only to provide the view access to all assets.
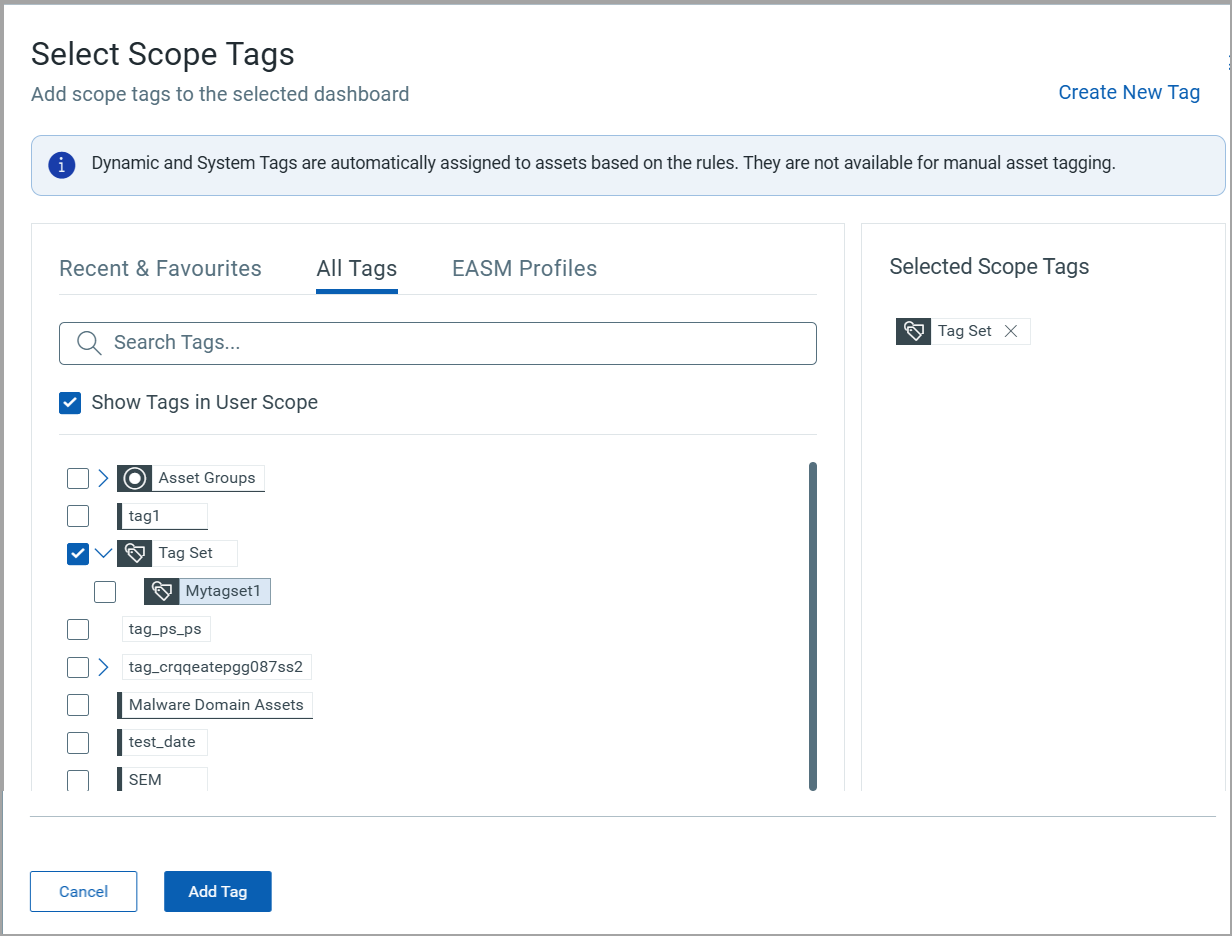
Include Tags
Select tags to add to the scope of selected users. You can also select Tag Sets.
Example:
Exclude Agent Assets from IP Range Tags
Choose to exclude agent assets from IP range tags as per your requirement.
Transfer Personal Configuration
The checkbox is available for selection when you edit the user.
Transfer Asset Groups
The checkbox is available for selection when you edit the user.